Latest bulletins in quantum computing have introduced renewed consideration to the query of how these advances might influence Bitcoin. In a newly revealed report, we offer an outline of the present state of quantum computing, the risk mannequin for Bitcoin, and the subsequent steps being thought-about. This submit gives a abstract of our key findings and suggestions. See the total report here.
Timeline for Bitcoin Preparation to Quantum Computing
We define a dual-track migration technique for Bitcoin in response to the potential emergence of quantum computing.
- Lengthy-Time period Path: This complete strategy assumes that there’s nonetheless a considerable window of time earlier than quantum computing poses a sensible risk. Drawing on the timelines of prior protocol upgrades akin to SegWit and Taproot, we estimate that implementing a full quantum-safe transition might take roughly 7 years.
- Quick-Time period Contingency Path: This monitor serves as an emergency response within the occasion of a sudden breakthrough in quantum computing. It prioritizes a speedy deployment of protecting measures to safe the Bitcoin community and could possibly be executed in roughly 2 years.
In each eventualities, funds which can be fastidiously managed, i.e., saved in hashed deal with varieties like P2PKH or P2WPKH with out deal with reuse, are already protected against quantum assaults. Nevertheless, spending these funds in a post-quantum safe means would require extra infrastructure, which is predicted to be developed throughout the second part of both timeline
Quantum Computer systems: When Are They Coming, and What Will They Be Succesful Of?
If realized at scale, quantum computing might supply vital speed-ups for particular lessons of issues by harnessing the ideas of quantum mechanics. Of explicit concern are cryptographically related quantum computer systems (CRQCs), machines able to breaking the mathematical assumptions underlying trendy cryptography. This contains algorithms like Elliptic Curve Cryptography (ECC), which is prime to Bitcoin’s safety.
Whereas quantum computing has been an lively space of theoretical analysis for many years, vital engineering challenges stay in constructing large-scale quantum machines, particularly CRQCs. So far, no quantum pc has surpassed classical supercomputers in fixing commercially related issues, nor demonstrated the capabilities wanted to threaten trendy cryptography.
Estimated timelines for CRQCs
Technological progress is notoriously onerous to foretell, it hardly ever follows a linear path, and historical past gives many examples of sudden breakthroughs. In anticipation of potential shifts within the cryptographic panorama, a number of organizations have proposed timelines for transitioning cryptographic signatures.
One of the vital distinguished efforts comes from the U.S. Nationwide Institute of Requirements and Know-how (NIST), which has been main the event of cryptographic requirements. Their revealed suggestions spotlight two key dates:
- By 2030, conventional encryption strategies, akin to ECDSA and RSA, needs to be phased out.
- By 2035, all cryptographic methods ought to transition totally to post-quantum algorithms.
The UK’s Nationwide Cyber Safety Centre follows a comparable strategy with a three-phase migration framework that goals to finish the transition to post-quantum cryptography by 2035. Different entities, such because the EU and China, are additionally actively engaged on post-quantum cryptography methods, although they haven’t but revealed formal timelines.
On the trade degree, a number of main firms, together with Cloudflare, Sign, and Google, have begun adopting post-quantum cryptography. They’re implementing hybrid signature schemes that mix conventional encryption strategies with post-quantum algorithms, requiring an attacker to interrupt each as a way to compromise the system. Apple has additionally introduced plans to transition to post-quantum cryptography. As PQC turns into an rising trade customary, extra firms are anticipated to comply with swimsuit.
What’s at Stake?
The monetary stakes of the risk to Bitcoin are substantial. Fig 2 illustrates evaluation revealing that roughly ~6.51 million bitcoin, value over $700 billion at present valuations, and representing 32.7% of present provide, is quantum susceptible. This contains funds held in addresses which have practiced deal with reuse, funds secured by inherently quantum-vulnerable script varieties, and funds which can be susceptible through public key publicity on forks of Bitcoin, akin to Bitcoin Money.
Bitcoin Risk Mannequin: What Ought to We Be Frightened About?
Quantum computing is predicted to influence two key areas of Bitcoin: mining and transaction signatures. In quantum mining, the issue of mixing the facility of a number of machines provides a disproportionate benefit to massive quantum miners, threatening decentralization. For transaction signatures, the chance is extra direct, a CRQC might derive non-public keys from public keys, enabling theft of funds.
Importantly, the timelines for these two threats differ considerably. Constructing a quantum pc that may outperform trendy ASIC miners presents a far better engineering problem than developing one able to breaking digital signatures. That is due, partly, to the low clock speeds of quantum processors, that are a lot slower than the extremely optimized and specialised {hardware} utilized in Bitcoin mining and the shortage of parallelization.
Signatures
A CRQC might break the idea that it’s infeasible to derive a non-public key from its corresponding public key below ECC primarily based schemes, doubtlessly permitting attackers to steal funds. In Bitcoin, possession of a UTXO is confirmed by signing a transaction with the non-public key akin to a given public key. If a CRQC can derive that personal key from the general public key, it may possibly falsely declare possession and spend the funds.
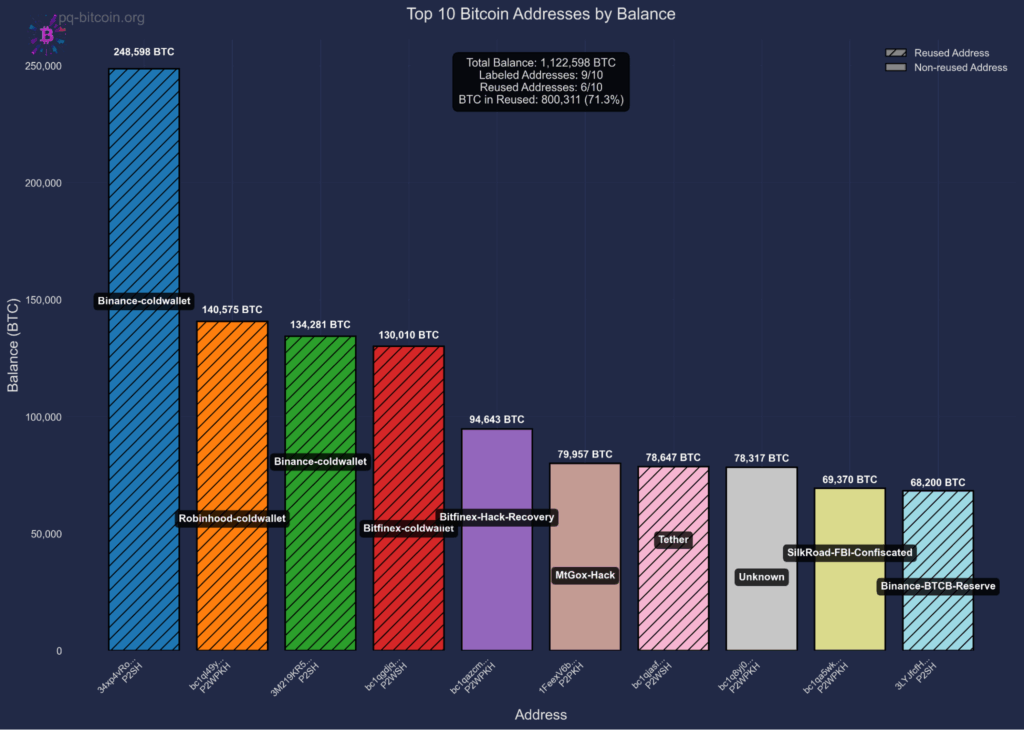
This results in two distinct quantum assault eventualities. When spending from hashed addresses, public keys are revealed quickly, giving attackers a short window, usually minutes to hours, to derive non-public keys and steal funds, presumably by means of chain reorganization. In distinction, sure output varieties (P2PK, P2MS, P2TR) expose public keys completely on-chain from the second funds are acquired, giving attackers limitless time to mount quantum assaults. Handle reuse converts the non permanent vulnerability of hashed addresses into everlasting publicity, as public keys stay seen on-chain after the primary spend. As proven in Fig 3, essentially the most susceptible targets are addresses that maintain vital funds with uncovered public keys akin to institutional holdings that practiced deal with reuse.
Mining
Bitcoin mining is predicated on the precept that the chance of discovering a sound block scales linearly with the quantity of computational effort expended. Grover’s algorithm, a quantum search approach, gives a quadratic speedup for brute-force search. Nevertheless, not like classical mining, Grover’s algorithm shouldn’t be simply parallelizable. This limitation might give a disproportionate benefit to entities with entry to large-scale, centralized quantum {hardware}, doubtlessly growing mining centralization slightly than broadening participation.
Along with considerations about centralization, quantum mining might alter miners’ optimum methods, doubtlessly degrading chain high quality, for instance, by growing the speed of stale blocks. A better stale block fee could make sure assaults (akin to egocentric mining or double-spends) less expensive and extra possible.
As famous earlier, constructing a quantum pc able to outperforming trendy ASIC miners is believed to be a lot farther off than creating CRQCs. As such, quantum mining shouldn’t be a right away concern and is unlikely to be a sensible risk within the coming many years. However, exploring Proof-of-Work mechanisms in a future quantum context stays a worthwhile analysis path. Growing a greater understanding of the potential dangers and mitigation methods would assist the ecosystem put together for a world the place quantum mining turns into possible.
Migration to Quantum Safety: What are the principle challenges?
Quantum-Safe Signatures
Quantum-secure cryptographic signatures have been studied for many years, however curiosity and progress have accelerated lately. This has led to the event of candidate protocols akin to SPHINCS+, FALCON, and others. Nevertheless, as a comparatively younger area, it has seen a number of proposed schemes initially believed to be safe however have been later damaged (e.g. SIKE), even by classical computer systems. Whereas belief within the present candidates is rising over time, the sphere stays lively and evolving.
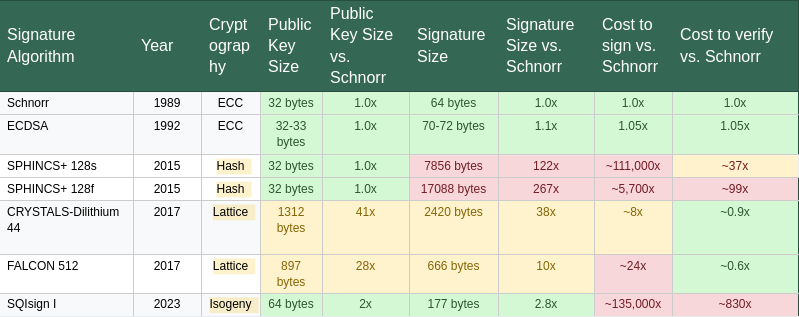
As detailed in Desk 1, a major limitation of post-quantum signature schemes is their considerably bigger key and signature sizes, together with elevated verification occasions, relative to classical algorithms akin to ECDSA and Schnorr which can be presently utilized in Bitcoin. To handle this, some proposals recommend leveraging SegWit’s witness low cost mechanism to scale back on-chain footprint. Nevertheless, the very best strategy for integrating quantum-secure signatures into the protocol stays an open query. Along with efficiency trade-offs, quantum-secure schemes don’t but help the total vary of performance offered by classical signatures, akin to these relied upon within the Lightning Community and different functions. This space continues to be an lively focus of analysis throughout the cryptography neighborhood, and additional enhancements are anticipated within the coming years.
Migration Pathways
If the Bitcoin neighborhood chooses emigrate susceptible funds to quantum-resistant codecs, a lot of UTXOs will have to be moved. A number of approaches are into consideration, every making completely different tradeoffs. Some deal with enabling safe spending of hashed-address outputs with out exposing the general public key prematurely. Others suggest mechanisms to restrict or regulate the spending of UTXOs which can be instantly susceptible to quantum theft. These methods usually require adjustments to consensus guidelines, akin to delicate forks, and should additionally account for the sensible problem of shifting a big quantity of UTXOs, doubtlessly taking 4 to 18 months even with sustained allocation of block area.
Philosophical Dilemma: Will we permit funds to be stolen?
The Bitcoin neighborhood faces a basic philosophical query: ought to quantum-vulnerable funds be made completely unspendable (“burned”) or stay accessible to quantum computer systems (“stolen”)? This choice touches Bitcoin’s core ideas of property rights, censorship resistance, and immutability. The burn strategy treats quantum vulnerability as a protocol bug requiring a conservative repair, stopping wealth redistribution to those that win the CRQC race. The steal strategy maintains that burning funds violates the property rights of their house owners, successfully confiscating property from those that might merely be unaware of the risk or unable emigrate in time.
The implications prolong past philosophy to market dynamics. A coordinated burn would completely take away thousands and thousands of bitcoins from circulation, doubtlessly growing the worth of remaining cash whereas offering market certainty. Permitting quantum theft allows large wealth switch to entities with quantum capabilities, doubtlessly creating extended market uncertainty and volatility as funds are steadily drained. A call on this matter is a defining second for Bitcoin’s governance mannequin, requiring the neighborhood to steadiness safety imperatives towards foundational ideas of person sovereignty and non-intervention.
So, what’s subsequent?
The arrival of CRQCs would mark a serious shift throughout the digital panorama, putting a lot of at this time’s safe communication, authentication, and digital infrastructure in danger. Whereas quantum computing shouldn’t be but a sensible actuality, preparations are underway to assist guarantee Bitcoin’s resilience towards future developments. Analysis continues throughout each the cryptographic and Bitcoin communities to evaluate potential dangers and discover sensible responses. Our report highlights two areas that will warrant near-term consideration: stopping deal with reuse and evaluating the trade-offs within the Burn vs. Steal dialogue round uncovered funds.
The window for proactive motion is open now, although it could not stay open indefinitely. Staying knowledgeable about advances in quantum computing and cryptography is important, as is finding out potential mitigation methods and their broader implications for the Bitcoin ecosystem. Guaranteeing Bitcoin’s long-term safety in a post-quantum world requires considerate, deliberate work, beginning now, so we will make well-informed selections whereas time continues to be on our facet.
This can be a visitor submit by Clara Shikhelman and Anthony Milton. Opinions expressed are solely their very own and don’t essentially replicate these of BTC Inc or Bitcoin Journal.
